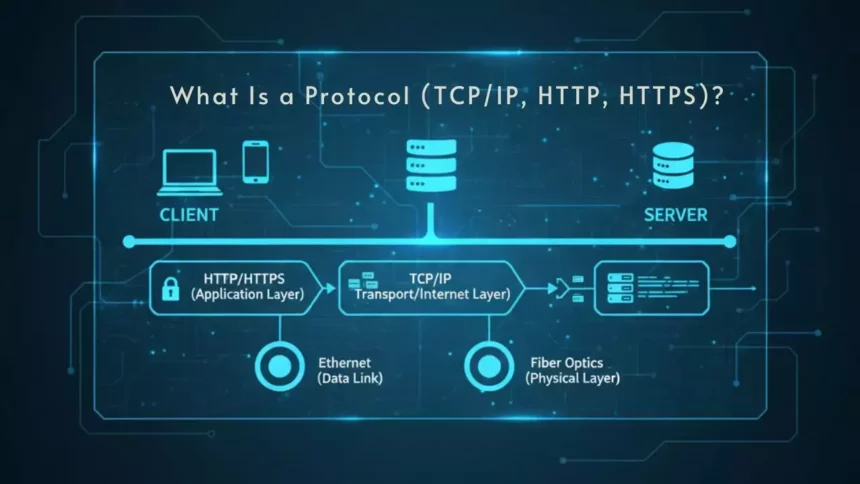
In the vast digital landscape we navigate daily, network protocols act as the unsung heroes that keep everything connected and functioning smoothly. Whether you’re browsing a website, sending an email, or streaming a video, protocols like TCP/IP, HTTP, and HTTPS are the foundational rules that govern how data travels across the internet. As an expert in the field, I’ll break this down for you in a conversational way, drawing from established knowledge and recent insights to provide a fresh, comprehensive perspective. By the end of this article, you’ll not only understand what these protocols are but also how they shape our online experiences in 2025 and beyond.

Let’s start at the basics. A protocol is essentially a set of standardized rules that devices use to communicate with each other over a network. Think of it like a common language spoken by computers, servers, and routers to ensure that data is transmitted accurately and efficiently. Without protocols, the internet as we know it would be chaotic, data packets could get lost, corrupted, or misinterpreted. In this article, we’ll dive deep into three key protocols: TCP/IP, the backbone of internet communication; HTTP, which powers web interactions; and HTTPS, its secure counterpart. We’ll explore their origins, mechanics, differences, and real-world applications, all while keeping things practical and insightful.
- See more:What Is a WAN (Wide Area Network)
What Exactly Is a Protocol?
Before we zoom in on specific examples, let’s establish a solid foundation. A protocol in networking is a predefined framework that outlines how data should be formatted, transmitted, received, and processed. It’s similar to how diplomats follow diplomatic protocols during international meetings to avoid misunderstandings. In the digital realm, protocols operate at various layers of the network stack, as defined by models like the OSI model, which categorizes communication into seven layers for clarity.
At its core, a protocol ensures reliability, efficiency, and security in data exchange. For instance, when you send a message over the internet, the protocol breaks it into smaller packets, routes them through the best available paths, and reassembles them at the destination. This is crucial in today’s interconnected world, where billions of devices, from smartphones to smart home systems, exchange data every second.
One of the most fundamental protocol suites is TCP/IP, which we’ll discuss next. Developed in the late 1970s as part of U.S. Department of Defense research, TCP/IP has evolved into the standard for internet communication. It’s not just one protocol but a collection that works together seamlessly. According to general knowledge from networking history, TCP/IP was designed to be robust, allowing data to travel across unreliable networks without losing integrity.
In practice, protocols like HTTP and HTTPS build upon TCP/IP to handle specific tasks, such as web page requests. HTTP, or Hypertext Transfer Protocol, is what your browser uses to fetch information from a server, while HTTPS adds an extra layer of encryption for secure transactions. These protocols are part of the application layer in the network model, meaning they deal directly with user interactions.
To make this more relatable, imagine ordering food online. TCP/IP handles the underlying delivery of your order from your device to the restaurant’s system, ensuring it arrives intact. HTTP is like the menu interface that lets you browse options, and HTTPS ensures your payment details are protected from prying eyes. As we progress, we’ll see how these elements interconnect in everyday scenarios.
Diving Deeper into TCP/IP: The Internet’s Foundation
Let’s turn our attention to TCP/IP, often hailed as the “protocol suite” that powers the global internet. TCP/IP stands for Transmission Control Protocol/Internet Protocol, and it’s a layered framework that manages how data moves from one point to another. This suite was originally developed for the ARPANET, a precursor to the modern internet, and has since become ubiquitous.
At its heart, TCP/IP consists of two main protocols: TCP (Transmission Control Protocol) and IP (Internet Protocol). TCP is responsible for reliable data delivery. It breaks data into packets, numbers them, and ensures they’re reassembled in the correct order at the receiving end. If a packet goes missing, TCP requests a resend, making it ideal for applications where accuracy is paramount, like file transfers or video calls.
On the other hand, IP handles the addressing and routing of these packets. Every device on a network has an IP address, a unique identifier that acts like a postal code for digital mail. When you type a website URL into your browser, IP determines the most efficient path for the data packets to reach the server. Versions like IPv4 and IPv6 address the growing number of connected devices; IPv6, for example, supports a vastly larger address space to accommodate the Internet of Things (IoT) boom we’re seeing in 2025.
The structure of TCP/IP is often visualized as a four-layer model: the link layer (for physical connections), the internet layer (IP‘s domain), the transport layer (TCP‘s role), and the application layer (where higher-level protocols like HTTP operate). This modularity allows for flexibility; for instance, if you’re using a wireless network, the link layer might involve Wi-Fi standards, while TCP/IP ensures the data gets to its destination regardless.
In real-world applications, TCP/IP is everywhere. From corporate networks using DNS (Domain Name System) to resolve website names to IP addresses, to IoT devices in smart cities exchanging sensor data, this protocol suite is indispensable. Recent trends in 2025 highlight its adaptation to emerging technologies like 5G and edge computing, where low-latency communication is key. For example, autonomous vehicles rely on TCP/IP for real-time data sharing with traffic systems, ensuring safe navigation.
One interesting insight from general networking knowledge is how TCP/IP promotes interoperability. Devices from different manufacturers can communicate seamlessly because they all adhere to the same standards. However, this openness also introduces security challenges, which is where protocols like HTTPS come into play.
Exploring HTTP and HTTPS: The Web’s Language
Now, let’s shift to HTTP and HTTPS, which are application-layer protocols that facilitate web communication. HTTP, or Hypertext Transfer Protocol, is the standard method for transferring hypertext documents across the internet. When you visit a website, your browser sends an HTTP request to the server, which responds with the requested data, like HTML pages or images.
HTTP operates on a client-server model. The client (your browser) initiates a request, and the server responds. Common methods include GET (to retrieve data), POST (to send data, like form submissions), and PUT (to update resources). It’s straightforward and efficient for non-sensitive interactions, but it lacks built-in security, meaning data is transmitted in plain text.
This is where HTTPS shines. HTTPS, or Hypertext Transfer Protocol Secure, is essentially HTTP with encryption added via SSL/TLS (Secure Sockets Layer/Transport Layer Security). It ensures that data exchanged between your browser and the server is encrypted, protecting it from interception. In 2025, with rising cyber threats, HTTPS has become the default for most websites, as mandated by standards like those from Google for better search rankings.
The evolution of HTTP includes versions like HTTP/1.1, HTTP/2, and now HTTP/3. HTTP/3, introduced in 2022, uses QUIC (a transport protocol based on UDP) instead of TCP, offering faster connections and better performance in high-latency environments. This shift reduces the time it takes for web pages to load, which is crucial for mobile users and streaming services.
To illustrate the differences, consider a comparison table:
| Feature | HTTP | HTTPS |
|---|---|---|
| Encryption | None; data is sent in plain text | Uses SSL/TLS for encryption |
| Security | Vulnerable to eavesdropping and tampering | Protects against man-in-the-middle attacks |
| Performance | Faster for simple requests | Slightly slower due to encryption overhead, but optimized in HTTP/3 |
| Use Cases | Non-sensitive sites, like public information pages | Banking, e-commerce, and any site handling personal data |
This table highlights how HTTPS builds on HTTP to address modern security needs. In practice, when you see a padlock icon in your browser’s address bar, it’s a sign that HTTPS is in use, encrypting your session.
How TCP/IP, HTTP, and HTTPS Work Together
These protocols don’t operate in isolation; they form a cohesive system. TCP/IP provides the underlying transport and routing, while HTTP or HTTPS handles the application-level exchange. For example, when you enter a URL like “https://www.example.com,” your browser first uses DNS (part of TCP/IP) to resolve the domain name to an IP address. Then, it establishes a TCP connection to that address and sends an HTTPS request over it.
In a typical web session, the process involves:
1. Handshake: TCP performs a three-way handshake to establish a reliable connection.
2. Data Transmission: HTTP or HTTPS sends requests and receives responses.
3. Closure: The connection is gracefully closed once the transaction is complete.
This interplay is evident in everyday activities, such as online shopping. Your credit card details are encrypted via HTTPS, routed securely through TCP/IP, and delivered to the merchant’s server. In 2025, with the rise of Web3 and decentralized applications, these protocols are adapting to support blockchain-based communications, ensuring data integrity in peer-to-peer networks.
Real-World Applications and Challenges
Protocols like TCP/IP, HTTP, and HTTPS underpin countless applications. In e-commerce, HTTPS secures transactions; in healthcare, TCP/IP enables telemedicine platforms to transmit patient data reliably; and in education, HTTP delivers online course materials. Emerging trends, such as augmented reality (AR) and virtual reality (VR), rely on these protocols for low-latency interactions.
However, challenges persist. Network congestion can slow down TCP-based connections, which is why HTTP/3‘s use of QUIC on UDP is gaining traction, it allows for quicker recovery from packet loss. Security threats, like DDoS attacks, target TCP/IP vulnerabilities, necessitating firewalls and intrusion detection systems.
As an expert, I’d advise implementing best practices: always use HTTPS for websites, regularly update your network protocols, and monitor traffic with tools like Wireshark for analysis. In the future, we might see more integration with quantum-resistant encryption to safeguard against advanced threats.
The Future of Protocols in a Connected World
Looking ahead to 2025 and beyond, protocols are evolving rapidly. HTTP/3 is just the beginning, with potential advancements in zero-trust architectures and AI-optimized routing. TCP/IP continues to adapt, with extensions for IPv6 enhancing scalability. The key is balancing speed, security, and accessibility as we move toward a more interconnected digital ecosystem.
In conclusion, understanding TCP/IP, HTTP, and HTTPS isn’t just about technical knowledge, it’s about appreciating the invisible infrastructure that makes our digital lives possible. By grasping these concepts, you’re better equipped to navigate, secure, and innovate in an increasingly online world.
Frequently Asked Questions
What is the main difference between TCP and IP?
TCP and IP are both part of the TCP/IP suite, but they serve distinct purposes. TCP focuses on reliable data delivery by establishing connections, managing packet order, and ensuring error-free transmission. In contrast, IP handles the addressing and routing of packets across networks, acting as the delivery mechanism without guaranteeing reliability. Together, they form a robust framework for internet communication, with TCP adding the layer of assurance that data arrives intact, which is essential for applications like email and file sharing.
How does HTTP differ from HTTPS in terms of security?
HTTP transmits data in plain text, making it susceptible to interception and tampering by malicious actors. HTTPS, however, encrypts this data using SSL/TLS protocols, ensuring that even if someone intercepts the information, it’s unreadable without the proper decryption key. This added security is crucial for protecting sensitive data, such as login credentials or financial details, and is why most modern websites enforce HTTPS by default in 2025.
Why is TCP/IP considered the backbone of the internet?
TCP/IP is the internet’s backbone because it provides a standardized, flexible architecture for data transmission across diverse networks. Developed from military research, it allows for interoperability between different devices and systems, ensuring that data can travel reliably from source to destination. Its layered design supports scalability, which has been key to the internet’s growth, accommodating everything from simple web browsing to complex IoT ecosystems.
Can HTTP work without TCP/IP?
No, HTTP typically relies on TCP/IP for its underlying transport. HTTP operates at the application layer, using TCP for reliable connections and IP for addressing. While newer versions like HTTP/3 use QUIC over UDP for better performance, they still build upon core internet protocols. In most cases, TCP/IP is essential for HTTP to function effectively in a networked environment.
What are the advantages of using HTTP/3 over previous versions?
HTTP/3 offers several advantages, including reduced latency and improved resilience to network issues, thanks to its use of QUIC on UDP. Unlike HTTP/1.1 and HTTP/2, which depend on TCP, HTTP/3 minimizes the impact of packet loss and supports multiplexing, allowing multiple streams over a single connection. This makes it ideal for mobile and high-speed applications in 2025, enhancing user experiences on platforms like video streaming services.
How do protocols like TCP/IP handle network congestion?
TCP/IP manages network congestion through mechanisms in TCP, such as congestion control algorithms that detect when the network is overloaded and adjust the sending rate accordingly. For example, if packets are being dropped, TCP slows down transmission to prevent further issues. This adaptive approach ensures efficient use of bandwidth, though it can sometimes lead to delays; advancements in 2025, like AI-driven optimizations, are making these processes even smarter.
Is HTTPS necessary for all websites?
In most cases, yes, HTTPS is necessary for websites handling any form of user data, due to increasing regulatory requirements and security best practices. It not only protects against data breaches but also boosts trust and SEO rankings. Even for non-sensitive sites, using HTTPS is recommended as a standard in 2025 to future-proof against evolving threats, though simple informational pages might still use HTTP if security isn’t a concern.
What role do protocols play in emerging technologies like 5G?
Protocols like TCP/IP are vital for 5G networks, enabling high-speed, low-latency communication for applications such as autonomous driving and smart cities. HTTP/3‘s efficient design complements 5G by reducing overhead, while TCP‘s reliability ensures critical data, like sensor readings, is transmitted accurately. As 5G rolls out globally, these protocols are being enhanced to support massive IoT deployments, making them foundational for the next wave of technological innovation.

Hi, I’m Nghia Vo: a computer hardware graduate, passionate PC hardware blogger, and entrepreneur with extensive hands-on experience building and upgrading computers for gaming, productivity, and business operations.
As the founder of Vonebuy.com, a verified ecommerce store under Vietnam’s Ministry of Industry and Trade, I combine my technical knowledge with real-world business applications to help users make confident decisions.
I specialize in no-nonsense guides on RAM overclocking, motherboard compatibility, SSD upgrades, and honest product reviews sharing everything I’ve tested and implemented for my customers and readers.